Today, Innokrea Team wants to tell you a bit about network scanning in an unusual context. Have you ever wondered how to scan the entire Internet in just a few minutes? Can you estimate the number of devices with certain, possibly vulnerable, software in this way? If we have piqued your interest, we encourage you to read on.
Classification of scans
In computer science, scans can be classified in many ways, depending on the level of authorization, the object of interest, or the location from which we operate. For example, the authors of this article distinguish the following types of scanning:
- based on direction
- external - accessible from the public network, such as the Internet
- internal - accessible from the local network, which assumes the compromise of the LAN
- based on authentication
- unauthenticated - the penetration tester or scanning software does not have required passwords or keys that elevate privileges. Its actions are limited.
- authenticated - the tester or software obtains required keys or passwords, enabling it to obtain more information
- based on scope
- limited - scanning a specific device and intended for that device
- comprehensive - scanning operating systems and all types
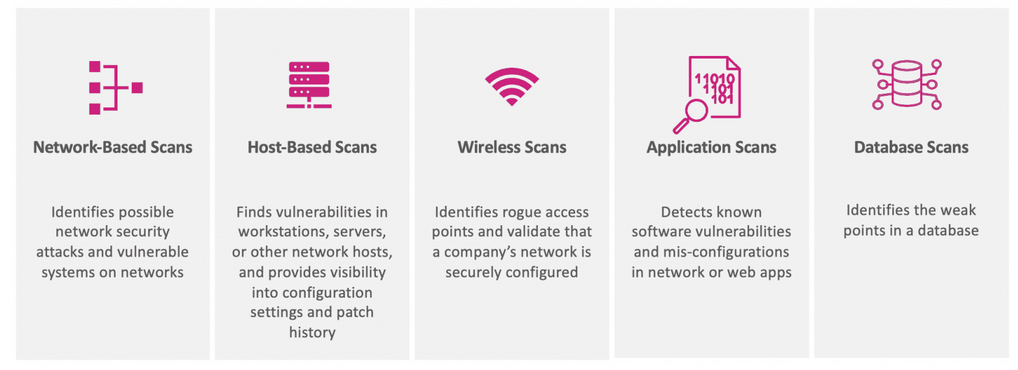
Figure 1: Scanner classification based on application. Source: balbix.com.
In addition, we distinguish scanners that occur on a host, in a computer network as dedicated devices (wirelessly or wired), and those used to detect vulnerabilities in Internet applications. What we use depends on business needs and what we want to achieve. The issue we want to address today is efficient scanning of the Internet, which is rarely seen in the context of devices intended for businesses. Regardless of the type of scan we choose and the needs we present, all solutions have a common feature - they automatically provide certain information about the infrastructure, which we can then process and draw conclusions from, and even take active actions.
Masscan - who, what, and why?
Masscan is a tool created by Robert Graham in 2013 for massive scanning of giant subnets. It works asynchronously and according to the documentation, is capable of sending even 10 million packets per second. It was written in C language, which, due to its low level of abstraction, is a difficult but very effective language.
Masscan can be used to:
- estimate the number of devices with a specific profile, e.g., having a vulnerable version of software
- scan massive amounts of devices to find ones with vulnerable software versions and break their security
Installation
If you don't want to install Masscan, we recommend using the Kali Linux system, where it is included in the base package of programs. If you want to install it on Linux, you need to execute the following commands:
sudo apt update
sudo apt install -y git gcc libpcap-dev
git clone https://github.com/robertdavidgraham/masscan
cd masscan
make
To test if the program is working, use the command
masscan --regression
Basic usage
Each element of an expression in Masscan that does not start with a "-" sign is perceived as an IP address in one of three formats, including as a range. There are also various ways to specify TCP and UDP ports: -p80 OR -p80,20-25 OR --ports U:123, U:100-125.
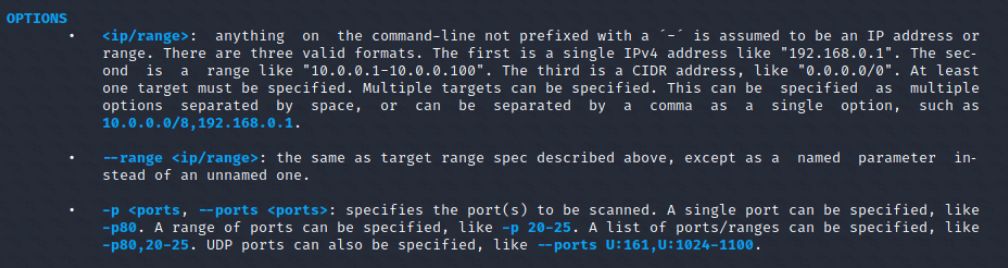
Figure 2: Fragment of the manual for the Masscan tool in Kali Linux.
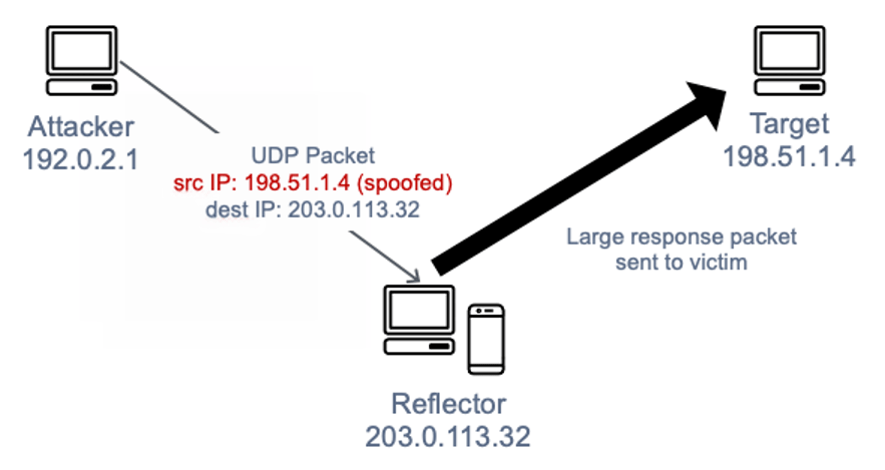
Masscan has a separate TCP/IP stack, which allows it to use a different IP address than that of the network card. In theory, any source address can be specified. It can be another public address or another address from our local subnet. Specifying the public address of another device as the source address can be used for a reflection attack. However, we do not necessarily have to change the IP address to use basic Masscan commands.
Example local network scan:
masscan 192.168.0.0/24 -p80 --rate 10000
We can also save the output of the command to a file:
masscan 12.0.0.0/8 -p80,443,3306 --echo > output.file
System limitations
It is worth noting that systems have limitations on sending and receiving a large number of packets. For Windows, this limit is up to 250,000 packets per second, and for new versions of Linux, it is up to 2 million packets per second. To exceed this limit, you must have an Intel 10Gb/s Ethernet connector and the PF_RING_DNA driver. It is available for both Windows and Linux systems.
More Masscan options - banner grabbing
To find out which services are running on the scanned target, you need to use a technique called "banner grabbing", which allows you to obtain information about a particular system in order to check the version of the software running on an open port. If the software is vulnerable, a hacker could use an exploit to gain access to the server. However, in order to obtain the appropriate information from the banner in Masscan, you need to change the source IP address to one from the same subnet - otherwise it will not work. Of course, the scanner allows you to change the source IP address of the packet using the parameter "--adapter-ip" or "--source-ip" (source-ip is not in the documentation, so it is better to use the first one). This is done because Masscan is not able to capture the banner from the default configured IP address. The "--adapter-ip" switch performs three basic tasks:
- Changes the source IP address
- Filters incoming packets so as not to discard those with this address
- Responds to ARP queries for this address
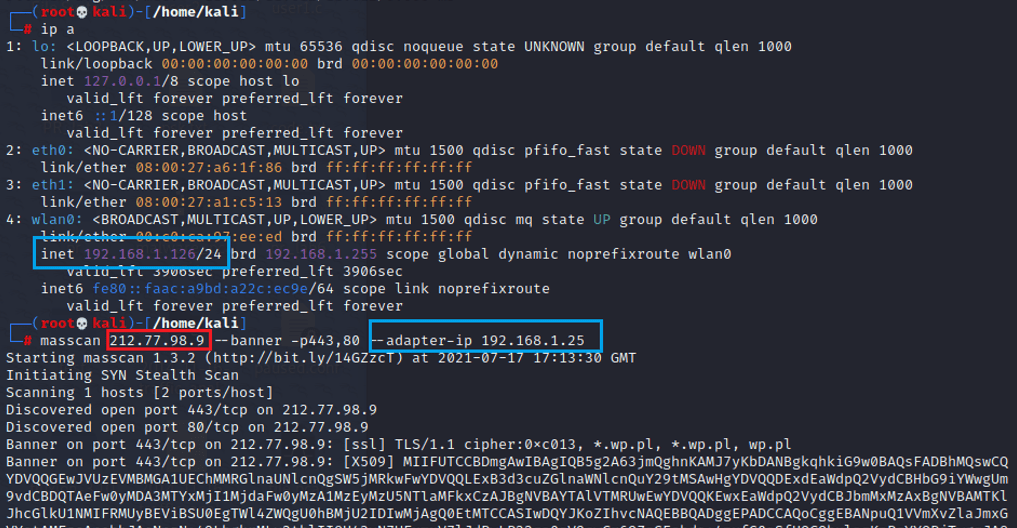
Figure 3: An example of capturing a banner for a web service. Note the IP address change.
In summary, for an Ethernet network, to capture a banner, simply enter the command with the "--banner" switch and change the source IP address (adapter-ip) to another one. When using a Wi-Fi network, an additional iptables rule will be required, which may look like this:
iptables -A INPUT -p tcp --dport 61000 -j DROP
Then, when using Masscan, you should always specify the source port you are using, for example:
masscan 12.0.0.0/8 --banners --source-port 61000
It may seem counterintuitive to use a port that we just blocked on the firewall. However, this is intentional and done so that the local TCP/IP stack does not see the incoming packet. Masscan can handle iptables rules because it bypasses this mechanism through the TCP/IP protocol stack. More information on this topic can be found at this link: https://github.com/robertdavidgraham/masscan.
Summary
In the second part of the article you will learn about advanced Masscan options, as well as what a reflection attack is. We are still in the topic of network scanning, so if you are interested in this topic, we encourage you to read it. See you!
Sources:
- https://snyk.io/learn/vulnerability-scanner/
- https://en.wikipedia.org/wiki/Banner_grabbing
- https://www.balbix.com/insights/what-to-know-about-vulnerability-scanning-and-tools/
- https://snyk.io/learn/vulnerability-scanner/
- https://github.com/robertdavidgraham/masscan
- https://www.slideshare.net/cisoplatform7/defcon-22grahammc-millantentlermasscaningtheinternet
- https://www.youtube.com/watch?v=yhd8277HrEw
- https://blog.erratasec.com/2018/10/masscan-as-lesson-in-tcpip.html
- https://docs.aws.amazon.com/whitepapers/latest/aws-best-practices-ddos-resiliency/infrastructure-layer-attacks.html
- https://www.nazwa.pl/pomoc/baza-wiedzy/co-to-jest-cache-memcached-i-jak-z-niego-skorzystac/
- https://www.cloudflare.com/learning/ddos/memcached-ddos-attack/
- https://www.wired.com/story/github-ddos-memcached/
- https://manpages.org/masscan/8