Green Data Centers – How to Choose an Eco-Friendly IT Partner?
A Guide for Companies Looking for IT Providers Using Energy-Efficient Infrastructure and Renewable Energy
 Author:
Author:Have you ever wondered how cybercriminals can take control of your company? Are the data of your customers and employees safe? At Innokrea, we want to show you the types of attacks you may be exposed to and how to defend against them. We will also provide technical details of these attacks so that your administrators know how to deal with cybersecurity threats. Today, we want to tell you about how connecting a found USB drive can lead to taking control of your computers.
Historical background
In the early 2000s, when the first USB flash drives hit the market, they were automatically played by Windows systems (98, XP, WS 2003). When a USB drive was plugged into a computer, the system started running the autorun.inf file. This created the possibility of an attack by placing a malicious executable file on the USB drive, and then writing a command in the autorun file to execute it. It could look like this:
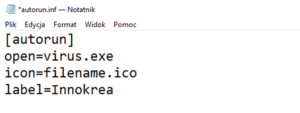
Photo 1: Example contents of the autorun.inf file.
Such system operation could be used to take over or damage a computer in a quick and unnoticed way – all that was needed was to plug in a USB drive for a few seconds. This option could be turned off in the settings or by modifying the system registry, but users were often unaware of this. Fortunately, in subsequent versions of the Windows operating system, Microsoft turned off the automatic execution of autorun files by default. Because Windows Vista was created at the turn of 2006/2007, such attacks could not occur for almost two years – until 2009, when a device called USB Rubber Ducky was created. Perhaps such devices existed earlier, but we are not aware of them. USB Rubber Ducky is still the most popular solution in the cybersecurity industry. This device was created by Darren Kitchen, an American who worked as an administrator and decided to automate repetitive tasks related to entering commands into computer terminals. The basic assumption of the device was not to take over the pentesting-hacker industry (if such existed in America at that time), but simply to save time on boring, cyclically performed administrative tasks. However, it soon turned out that such a device could be used by people who want to take over someone else’s computer in a very similar way to how attackers did it many years ago, by modifying the aforementioned autorun.inf file. How?

Photo 2: USB Rubber Ducky device from HAK5 shop
What is BadUSB?
The USB Rubber Ducky device is a miniature board shaped like a USB flash drive that presents itself to the system as a USB keyboard. It is a board that allows for the software programming of a keyboard in any way (within the limitations of a regular keyboard). In practice, this is much more dangerous than the autorun file known from older Windows systems, as it allows for lightning-fast modification of files on the disk, opening a terminal console and typing commands there at a speed of hundreds of characters per second. We don’t have to, but we can place executable files on the board’s memory – however, running such files on modern computers can be detected by the default Windows program detecting malicious software, Windows Defender, or other antivirus programs. On the other hand, opening a console does not cause any warnings. Additionally, if our home computer account has administrator privileges, we can execute even more (dangerous and invasive) commands on the victim’s computer.
Operation
Scripts written to perform specific commands on the victim’s computer usually have a very simple, primitive syntax and resemble the commands placed in an autorun file or those written in .bat files.
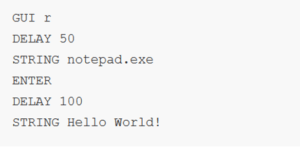
Photo 3: Example Rubber Ducky script
These scripts are the essence of what can be done with the help of BadUSB. From simple pranks that can be played on friends, such as swapping mouse buttons or flipping the screen, to stealing saved passwords of user accounts and sending them via email, or running programs that encrypt the victim’s disk or allow remote control. On Github, there are entire repositories containing hundreds of different scripts “for different occasions” – there are even programs that allow constant control over a specific device and report the device’s status via email.
The development of the Rubber Ducky
With the development of technology, the management of the USB Rubber Ducky has also progressed. New versions, often created by manufacturers other than the original HAK5 (such as Maltronics), support remote device management. Adding a wifi module to the device allows for the establishment of a local HTTP server, which serves as the management interface. There is also no longer a need to execute scripts using a computer. With a ducky device with remote wifi support, one can log into the server with a phone and run a script from anywhere, at any time. It should be noted that the use case scenario changes depending on the version of the device used – if the attacker is able to remotely operate the device, they can connect it to a computer while a colleague is absent from the office, and then, when the colleague logs into their account, run a few-second script to take control of their computer.
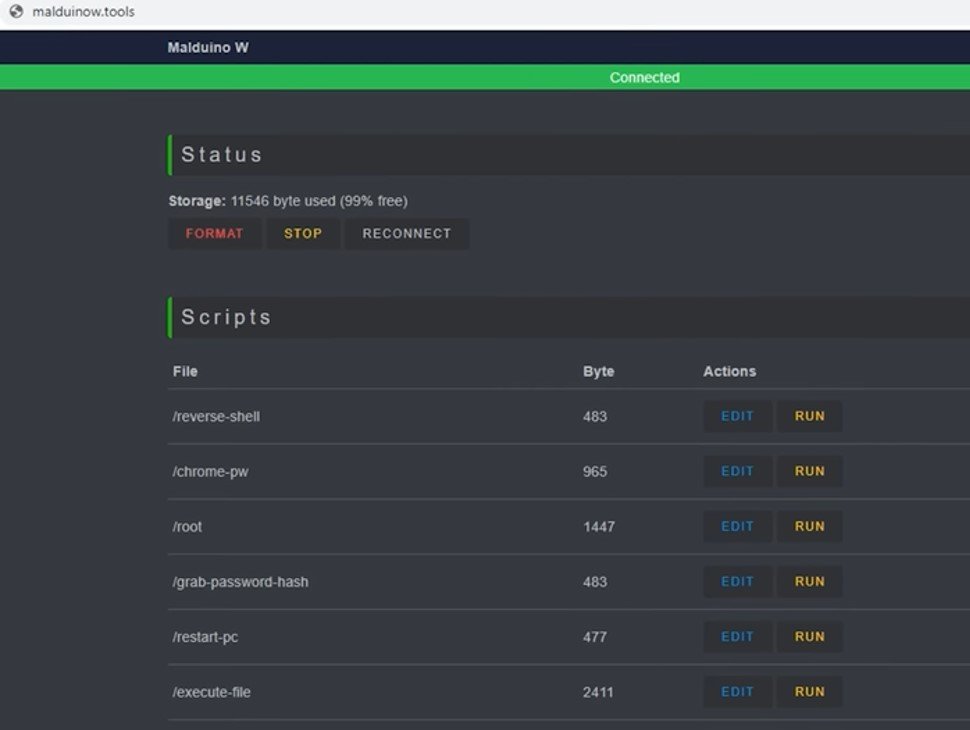
Photo 4: Admin panel of Malduino WiFi device
The possibilities of attack become wider and more flexible. Of course, as the company where such tests are performed grows, the possibilities of securing workstations also increase. This means that a penetration tester often cannot perform certain procedures due to limited user rights on a given computer. Then the matter becomes much more difficult, although there are ways to escalate one’s privileges using vulnerabilities found on their own or purchased on the Internet. However, this is much more difficult and requires the use of a wide range of hacking techniques and often a whole team of specialists.
In the next article, we will tell you about the possibilities of creating such a device at home, what USBKiller is, and how to defend against such threats.
Sources:

Green Data Centers – How to Choose an Eco-Friendly IT Partner?
A Guide for Companies Looking for IT Providers Using Energy-Efficient Infrastructure and Renewable Energy
Green IT

Helm for the Second Time – Versioning and Rollbacks for Your Application
We describe how to perform an update and rollback in Helm, how to flexibly overwrite values, and discover what templates are and how they work.
AdministrationInnovation

Helm – How to Simplify Kubernetes Management?
It's worth knowing! What is Helm, how to use it, and how does it make using a Kubernetes cluster easier?
AdministrationInnovation