Helm for the Second Time – Versioning and Rollbacks for Your Application
We describe how to perform an update and rollback in Helm, how to flexibly overwrite values, and discover what templates are and how they work.
 Author:
Author:We invite you to the second part of our considerations on ransomware (part 1 available here). What are real cases of attacks, and what are good defense practices in cyberspace for your company? We welcome you to read on!
Cases from other companies
One of the most prominent cases in recent years was the attack on Norsk Hydro, a giant in the aluminum industry. The attackers managed to gain access by having an employee open an email attachment that came from a trusted source (the mailbox of a trusted individual was compromised and used in the attack). Within a few days, the attackers were able to establish continuous access to the infrastructure, which they subsequently encrypted. This case is significant not only due to the financial scale (the company lost over 40 million dollars) but also because they chose to be transparent about it. They kept the company informed in real-time about the ongoing situation and how the IT teams were combating the threat, working to restore the company’s operations. If you’d like to read more about this topic, we recommend an article on Microsoft’s website regarding this specific attack.
Another significant ransomware attack that affected hundreds of thousands of computers worldwide was the so-called WannaCry. In 2017, hackers known as the Shadow Brokers exploited an advanced vulnerability called EternalBlue in the Windows operating system. This vulnerability was said to have originated from the U.S. National Security Agency (NSA) and had reportedly been used by government hackers (APT groups). EternalBlue targeted a flaw in the Microsoft Server Message Block 1.0 (SMBv1) protocol, using it to gain remote execution access to the victim’s computer with delivered code. Moreover, the virus had the capability to self-propagate across networks. Entities such as hospitals, universities, and automobile manufacturers were among those affected. The ransomware screen demanding payment even appeared on ATM screens
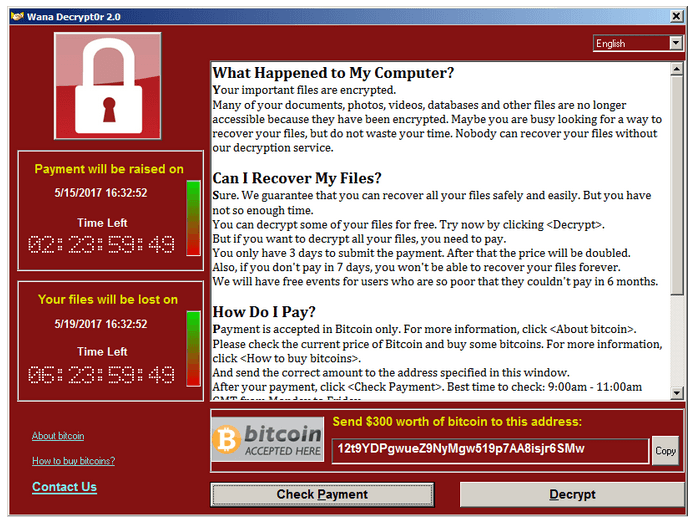
Figure 1 – Program window appearing after the execution of the WannaCry ransomware.

Figure 2 – Infected ATMs in China.
Best Practices
So, how can you protect yourself from ransomware attacks? There isn’t a single answer to that question because each company’s infrastructure is slightly different. However, you can adhere to generally accepted good security practices that will help minimize the threat and, in case of an attack, allow you to effectively recover your data.
Before we delve into tips specifically about ransomware, we encourage you to familiarize yourself with general security advice that Innokrea offers on our blog:
In addition to the practices we recommend, here’s what you should consider:
Summary
We hope this short series on ransomware has been useful and intriguing for you. Remember that we’re never completely safe in the cyber realm, but by employing proper cybersecurity practices and hiring knowledgeable individuals, we can protect our businesses and, in the event of a successful attack, minimize the losses incurred by the company. See you next week!
Sources:

Helm for the Second Time – Versioning and Rollbacks for Your Application
We describe how to perform an update and rollback in Helm, how to flexibly overwrite values, and discover what templates are and how they work.
AdministrationInnovation

Helm – How to Simplify Kubernetes Management?
It's worth knowing! What is Helm, how to use it, and how does it make using a Kubernetes cluster easier?
AdministrationInnovation

INNOKREA at Greentech Festival 2025® – how we won the green heart of Berlin
What does the future hold for green technologies, and how does our platform fit into the concept of recommerce? We report on our participation in the Greentech Festival in Berlin – see what we brought back from this inspiring event!
EventsGreen IT