Green Data Centers – How to Choose an Eco-Friendly IT Partner?
A Guide for Companies Looking for IT Providers Using Energy-Efficient Infrastructure and Renewable Energy
 Author:
Author:Dzisiaj jako INNOKREA opowiemy Wam czym jest ransomware, jak dostaje się do Waszych firm i co najważniejsze jakie dobre praktyki można stosować, aby zminimalizować ryzyko bycia ofiarą złośliwego oprogramowania. Jeśli jesteś zainteresowany, to zapraszamy do lektury!
Czym jest ransomware?
Ransomware to oprogramowanie, które po uzyskaniu dostępu do systemu komputerowego stara się zmusić ofiarę do zapłaty okupu. Może to następować poprzez blokadę dostępu do systemu komputerowego (zwykle szyfrowanie) i tym samym uniemożliwienie odczytu lub poprzez wykradanie danych dla danej firmy i groźbę ich upublicznienia. Strategia polegająca na kradzieży danych dobrze sprawdza się w przypadku danych wrażliwych, szczególnie gdy uderza to w wiarygodność przedsiębiorstwa np. w przypadku danych medycznych.
Pierwszy ransomware
Za pierwszy przypadek ransomware uznaje się wirusa stworzonego przez Joseph’a Popp’a, który szyfrował z pomocą kryptografii symetrycznej wszystkie foldery na dysku C. Wirus jest znany pod nazwą AIDS lub PC Cyborg Trojan. Rozprzestrzeniony został na 20 000 dyskietek do ponad 90 krajów. Na dyskietce miał znajdować się program, który na podstawie kwestionariusza potrafi przewidzieć, czy osoba jest zarażona AIDS, ale był na niej również złośliwy program działający po 90 uruchomieniach komputera. Wyświetlał on komunikat o konieczności zapłaty 189, a później 378 dolarów za odblokowanie systemu.
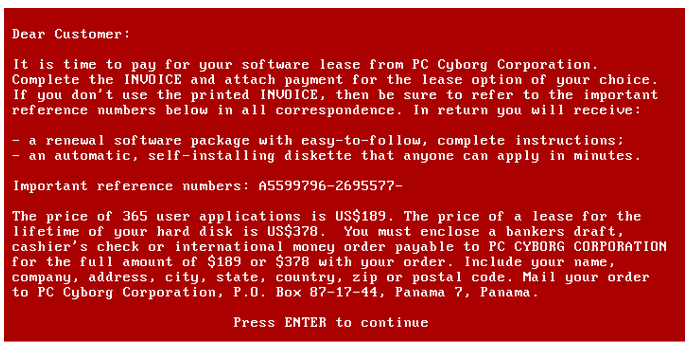
Rysunek 1 – PC Cyborg Trojan, wiadomość o wymaganej płatności, źródło: wikipedia.
Rysunek 2 – Inne przykłady domagania się okupu.
Jak ransomware dostaje się do firmy?
Sprawa nie jest oczywista jak haker dostaje się do firmy, ponieważ każda firma używa innego oprogramowania i jest narażona na inne rodzaje ataków. Można natomiast wyróżnić kilka sposobów, które są najbardziej popularne.
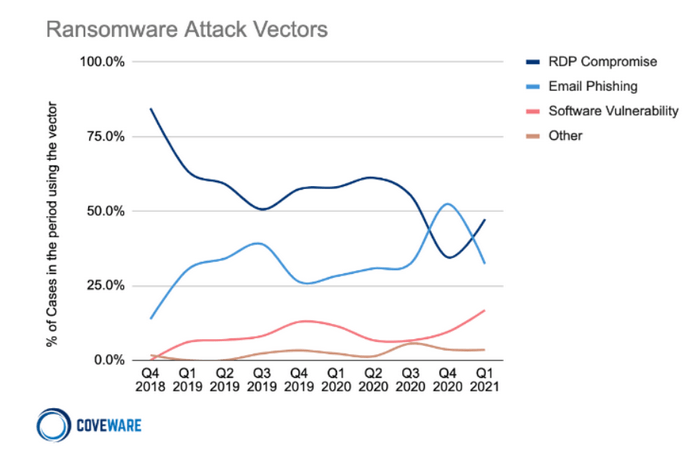
Rysunek 3 – Statystki dotyczące typów ataków do pierwszego kwartału 2021. Źródło: Coveware.
Remote Desktop Protocol, RDP to protokół pozwalający na zdalną komunikację z usługą terminala graficznego w Microsoft Windows. Usługa ta jest dostępna we wszystkich systemach operacyjnych Windows od wersji Windows 2000 za pomocą programu Pulpit Zdalny. Często występującym scenariuszem ataku z użyciem ransomware jest wynajdywanie wystawionych do Internetu komputerów z uruchomioną usługą RDP np. z użyciem Shodan’a. Jeśli dodatkowo używamy słabych haseł, lub domyślnych danych logowania to możemy w szybki sposób stać się ofiarą hakera. Zwykłe komputery użytkownika nie są narażone na taki atak, ponieważ z definicji nie są widoczne z Internetu. Najlepsze praktyki w przypadku tego protokołu mówią, że powinno się:
Innym sposobem często wykorzystywanym przez przestępców są maile phishingowe. O ile filtry spamu i oprogramowanie pocztowe są w dzisiejszych czasach przeważnie skuteczne do obrony przed większością wiadomości chcących zrobić firmie krzywdę, to jednak czasem zdarzają się wiadomości, które mogą być bardzo przekonywujące dla użytkownika. To z kolei może skutkować pobraniem załącznika np. docx ze złośliwym makrem, które doprowadzi do skompromitowania systemu. Należy także uważać na wiadomości od zaufanych kontrahentów. Jeśli taka skrzynka pocztowa zostanie przejęta, to może to znacząco podnosić wiarygodność przesyłanego załącznika a tym samym ataku. Bardzo ważnym jest prawidłowe wyszkolenie pracownika, aby był w stanie odróżniać maile phisingowe od standardowych, a także wielowarstwowa ochrona – od filtrów antyspamowych po programy zwiększające bezpieczeństwo danej stacji np. EDR, HIPS czy antywirusy.
Inne ataki mogą wynikać z błędów w konfiguracji czy oprogramowaniu i tutaj nie zawsze jesteśmy w stanie się ustrzec przed atakami, ale zawsze można zminimalizować jego konsekwencje poprzez wielowarstwową ochronę, odpowiednie monitorowanie oraz stworzenie procedur reagowania na incydenty.
Co po wykorzystaniu luki?
Kiedy przestępcy dostaną się do wewnętrznej infrastruktury danej firmy rozpoczynają kolejne etapy działania mające na celu rozpoznanie infrastruktury i zadanie szkód firmie. Przebieg ataku można przedstawić w następujący sposób:
Czy płacić okup?
Jest to ciężka, indywidualna decyzja dla każdej firmy. Należy mieć jednak świadomość, że czasem nawet po uiszczeniu okupu dane pozostają zaszyfrowane i nie ma żadnej gwarancji ich odzyskania. Zdarza się, że na rynku wskutek błędnej implementacji ransomware pojawia się dekryptor, który jest w stanie bez uiszczenia opłaty deszyfrować pliki. Jeśli firma posiada nieuszkodzone, izolowane kopie zapasowe to nie powinna mieć takich dylematów. Należy jednak wziąć pod uwagę, że czasem postawienie całej infrastruktury informatycznej od nowa i odzyskanie danych może trwać dni lub tygodnie. Firma Coveware w swoich najnowszych statystykach pokazuje jednak, że coraz więcej firm decyduje się nie płacić okupu i skorzystać ze swoich kopii zapasowych.
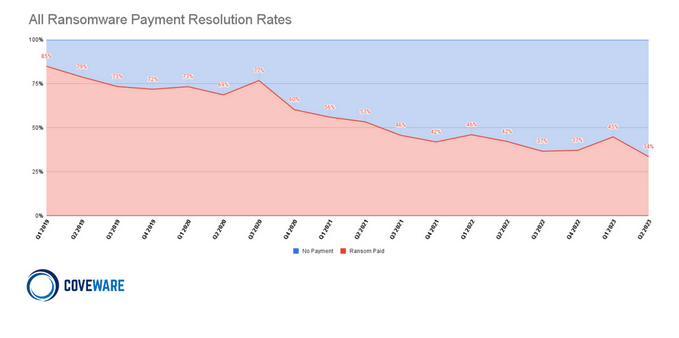
Rysunek 4 – Statystki opłacanych okupów w atakach typu ransomware. Źródło: Coveware.
Podsumowanie
Temat ransomware jest wieloaspektowy i ciężko udzielić jednoznacznej odpowiedzi jak firmy powinny sobie radzić z takimi incydentami. Za tydzień omówimy realne przykłady takich ataków i spojrzymy jak firmy na całym świecie poradziły sobie z takimi wyzwaniami.
Źródła:

Green Data Centers – How to Choose an Eco-Friendly IT Partner?
A Guide for Companies Looking for IT Providers Using Energy-Efficient Infrastructure and Renewable Energy
Green IT

Helm for the Second Time – Versioning and Rollbacks for Your Application
We describe how to perform an update and rollback in Helm, how to flexibly overwrite values, and discover what templates are and how they work.
AdministrationInnovation

Helm – How to Simplify Kubernetes Management?
It's worth knowing! What is Helm, how to use it, and how does it make using a Kubernetes cluster easier?
AdministrationInnovation