Today we want to tell you more about passwords and, most importantly, the attacks on passwords that await Internet users and programmers. Concepts related to hashes will also appear, so if you haven't read our previous article about hashing functions on our blog, we encourage you to do so. And now, we invite you to read!
Passwords – Prove it’s you
Some time ago in an article on the blog, we discussed authentication methods and identity-related issues for users. Passwords are one of the fundamental authentication methods, where users prove that they are who they claim to be. The entire process is based on the assumption that only the specific user knows the password (kept secret) and that the password isn't easily guessable. Long ago, when good practices for creating passwords didn't exist, people used single words, names, birthdates of loved ones, or simple numbers. Today, with the advancement of password-cracking techniques and increased computational power available, we know that such approaches are insufficient.
How Are Passwords Stored?
The answer is - it depends. It's often said that passwords shouldn't be encrypted and should be hashed instead. However, there are situations where applications do encrypt passwords, such as in password managers, where they must be stored as text rather than hashes. For example, the documentation for the 1Password manager states that their application uses AES-GCM-256 for encrypting passwords. In most cases, though, web applications should store passwords in the form of hashes rather than encrypting them.
Hashes and Web Applications
If a user creates an account in our application, the application should create the account by entering the appropriate database entry. The password the user chooses should be passed to a hash function, and the resulting fixed-length string should be stored together with the account entry in the database. Other mechanisms, such as "salt and pepper," can be added to our application, but let's focus on the basics for now.
If a user already has an account and tries to log in to the application, the application takes the password provided, hashes it again, and checks the entry in the database. If everything matches, the application grants the user access to their account (via SessionId or Token, for example)."
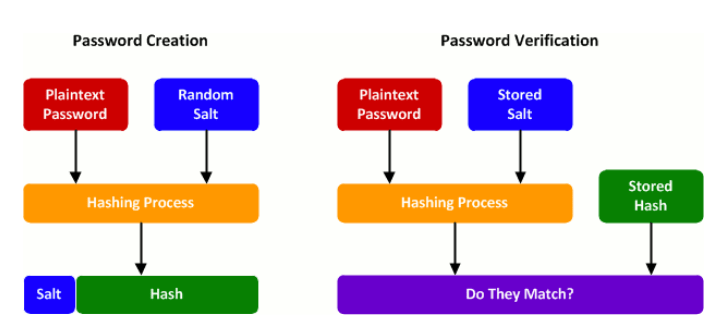
Figure 1 - Password Creation and Verification Process, Source: lucidoutsourcing
Hashing, as we remember, is a one-way mathematical function, meaning that the password cannot be retrieved from the resulting hash. This means that even if the database is breached, the hacker won't be able to recover the stored passwords - of course, provided that we use secure practices and correctly implement mechanisms.
Attack Methods
- To understand good practices more precisely, one would need to know the attack methods employed by hackers to breach password security. These include:
- brute force - a brute force attack involves checking all available combinations, whether character-based or numerical. If a hacker knows that a password has 8 letters and is constructed from lowercase letters, they have 26^8 combinations to try. All combinations can be checked in a few hours with the help of an ordinary computer. Attack scenarios could include cracking a obtained hash (by generating all 8-letter combinations and then comparing with our hash offline) or attempting to guess a password for an online application (one that won't ban our IP/address even after hundreds of requests - an online attack) or trying to break into a Wi-Fi network. With additional security mechanisms limiting the number of attempts or with sufficiently long, high-entropy passwords, such an attack is not feasible within a reasonable timeframe.
- rainbow tables - attacks using rainbow tables involve searching ready-made tables that contain hash-to-password mappings, saving time on generation and focusing solely on password searches. However, we need to know which hashing algorithm was used, as a different algorithm will return a different hash for each password. These tables can be found, for example, on sites like https://freerainbowtables.com/. It's simply an optimization of the brute-force attack. Adding a unique character sequence (a salt) to passwords stored in the database, individual for each user (also stored in the database), renders ready-made rainbow tables useless, even for common passwords. Additionally, users with the same passwords have different hashes due to the salt.
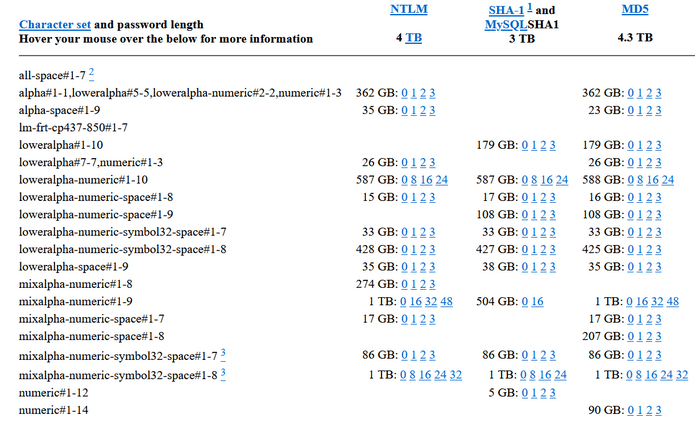
Figure 2 - Rainbow Tables for Different Password Policies and Hashing Algorithms. It's evident that these databases often weigh hundreds of gigabytes and do not include combinations with special characters (only alphanumeric/lower alpha or numeric)."
- Dictionary Attack - to limit the number of available combinations, this type of attack can be used. It involves utilizing or generating a personal dictionary of commonly used phrases in passwords and creating a restricted number of combinations. By aggregating passwords exposed in data breaches from various companies, hackers create publicly available dictionaries sorted by the most frequently used passwords, such as the well-known rockyou wordlist. By stealing poorly secured databases (passwords stored in plaintext, hashed with insecure hashing functions, or hashed without salt), hackers aggregate this data into lists and then use the most commonly used passwords in attacks. Additionally, tools like hashcat can be used, allowing us to generate derivatives of a given password like “password1,” “p@ssword,” or “p@sword123.” Scientific research also suggests that people naturally place numbers and special characters at the end of passwords.
- Spray Attack - this attack involves the hacker taking a few commonly used passwords and attempting to breach security by changing the login they want to use. Let's assume a hacker gains access to an application's database from our company, where passwords were correctly hashed. It's not worth performing a brute force attack, but armed with login details and knowing the most frequently used passwords on the Internet, they can try logging into each account using a few of these same passwords. Importantly, systems designed to detect multiple login attempts in an application may be ineffective, as the attacker tries to log into a different account each time. An offline spray attack is also possible if we want to crack hashes that aren't in rainbow tables.
- Pass-the-Hash Attack - if an application/system expects a hash instead of a password for user verification input, a leaked hash means that the password doesn't need to be known. If the attacker gains access to these hashed passwords (for example, by hacking into the system and inspecting operational or cache memory), they can directly use these encrypted passwords for network authentication without needing to use passwords in plain text. Therefore, a good practice is to hash only on the backend application side.
- Keylogger - if malware gets onto our computer, for instance, through a phishing email, the virus can inspect our computer and what we type to learn what our password is.
- Sniffing - if an attacker gains access to a network, they can attempt MITM attacks that allow them to inspect our traffic. Most of today's communication is encrypted, but by applying additional techniques (TLS downgrade, SSL stripping) and under certain assumptions, the attacker can steal our passwords.
- Reverse Engineering - attackers can try to analyze application code using reverse engineering tools to discover default system passwords embedded there. This is common in IoT solutions. Manufacturer embedding certain emergency system passwords is a severe oversight and could result from oversight at some stage of software production.
- Shoulder Surfing or Cameras - attackers can simply watch over our shoulder as we enter our password, or what we enter could be recorded on camera.
- Key-Wrench Attack - this is a type of physical attack where someone disregards cryptographic mechanisms and blackmails or tortures their victim until they provide their password.
- Other Attacks - the list of threats is, of course, not complete, and such a list cannot be created. Other attacks might utilize more advanced techniques dependent on the victim's employed technology.
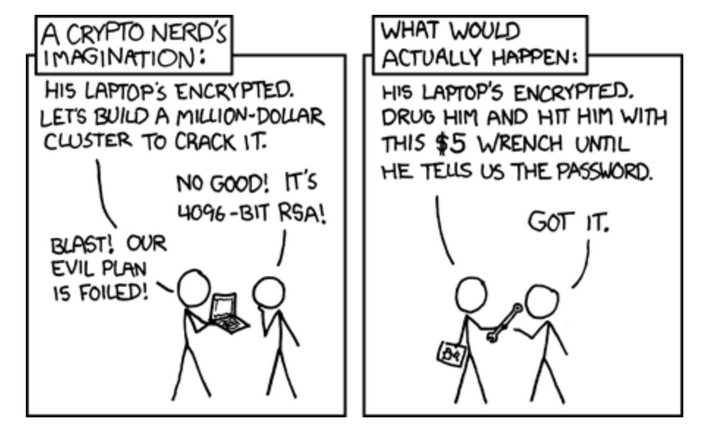
Figure 3 - Comic illustrating how, despite advanced technological security measures, overlooking physical threats can have disastrous consequences for security, Source: XKCD's Wrench Attack Cartoon
Summary
There are numerous types of attacks, varying in technicality. If you want your company to be secure, it's best to entrust security tasks to experts. The topic is quite extensive, but what you can do is read our articles about good cybersecurity practices to significantly reduce the chances of becoming a victim of an attack.
Next week, we will discuss good practices related to passwords - managing and storing them. Stay tuned!"
Sources: