Helm for the Second Time – Versioning and Rollbacks for Your Application
We describe how to perform an update and rollback in Helm, how to flexibly overwrite values, and discover what templates are and how they work.
 Author:
Author:Today, as INNOKREA, we will tell you about what ransomware is, how it infiltrates your companies, and most importantly, what best practices can be employed to minimize the risk of falling victim to malicious software. If you’re interested, we invite you to read on!
What is Ransomware?
Ransomware is software that, upon gaining access to a computer system, attempts to force the victim to pay a ransom. This can be achieved by blocking access to the computer system (usually through encryption), thereby preventing access, or by stealing data from a given company and threatening to make it public. The strategy of stealing data works particularly well for sensitive information, especially when it undermines a company’s credibility, such as in the case of medical data.
The First Ransomware
The first instance of ransomware is attributed to a virus created by Joseph Popp, which used symmetric cryptography to encrypt all folders on the C drive. The virus is known by the names AIDS or PC Cyborg Trojan. It was distributed on over 20,000 floppy disks to more than 90 countries. The floppy disk contained a program that, based on a questionnaire, claimed to predict whether a person was infected with AIDS. However, it also contained a malicious program that would activate after 90 computer restarts. This program displayed a message demanding a payment of $189, and later $378, to unlock the system.
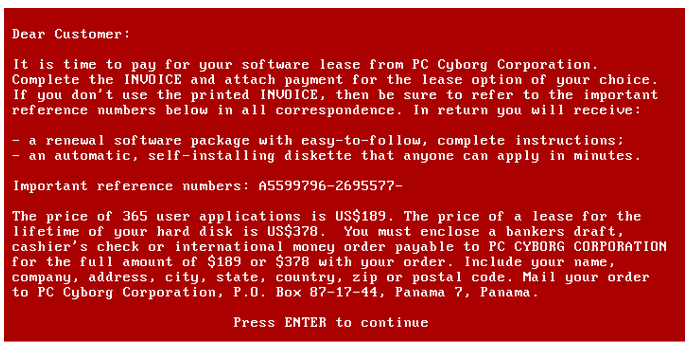
Figure 1 – PC Cyborg Trojan, message demanding payment, source: Wikipedia.
Figure 2 – Other examples of ransom demands.
How Does Ransomware Infiltrate a Company?
The matter of how hackers gain access to a company is not straightforward, as each company utilizes different software and is exposed to varying types of attacks. However, several methods can be distinguished, which are among the most popular.
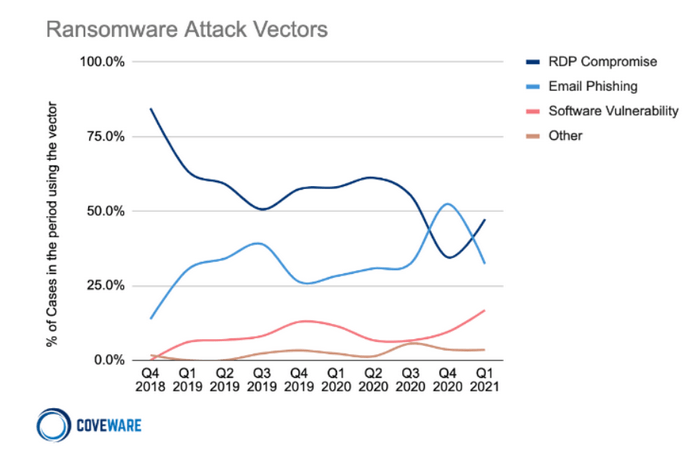
Figure 3 – Statistics on types of attacks for the first quarter of 2021. Source: Coveware.
Remote Desktop Protocol, RDP, is a protocol that enables remote communication with the graphical terminal service in Microsoft Windows. This service is available in all Windows operating systems from Windows 2000 onwards, using the Remote Desktop program. A commonly observed attack scenario involving ransomware is the discovery of computers with exposed RDP services on the Internet, often using tools like Shodan. If weak or default login credentials are used, one can quickly become a target for hackers. Regular user computers are not susceptible to such attacks, as they are, by definition, not visible from the Internet. Best practices for this protocol include:
Another commonly exploited method by criminals is through phishing emails. While spam filters and email security software are generally effective defenses against most messages attempting to harm a company, sometimes messages that are very convincing to the user can slip through. This can result in the downloading of attachments, such as malicious macros within a docx file, leading to system compromise. Caution should also be exercised with messages from trusted contacts. If such an email account is compromised, it can significantly boost the credibility of the attached file and, subsequently, the attack. Proper employee training is crucial for distinguishing phishing emails from genuine ones, and multi-layered protection, from anti-spam filters to security-enhancing programs like EDR, HIPS, or antivirus software, is vital.
Other attacks can stem from configuration or software errors, and here, we may not always be able to prevent attacks, but we can always minimize their consequences through multi-layered protection, proper monitoring, and incident response procedures.
What Happens After Exploiting a Vulnerability?
Once criminals gain access to a company’s internal infrastructure, they initiate subsequent stages of action aimed at reconnaissance and inflicting damage to the company. The attack process can be outlined as follows:
To Pay or Not to Pay Ransom?
This is a difficult, individual decision for each company. However, it’s important to be aware that sometimes, even after paying the ransom, the data remains encrypted, and there is no guarantee of recovery. Occasionally, due to faulty ransomware implementation, a decryptor emerges on the market that can decrypt files without payment. If a company has intact, isolated backup copies, it shouldn’t face such dilemmas. Nevertheless, it’s worth considering that rebuilding an entire IT infrastructure from scratch and recovering data can take days or weeks. However, in its latest statistics, Coveware indicates that an increasing number of companies choose not to pay the ransom and instead rely on their backup copies.
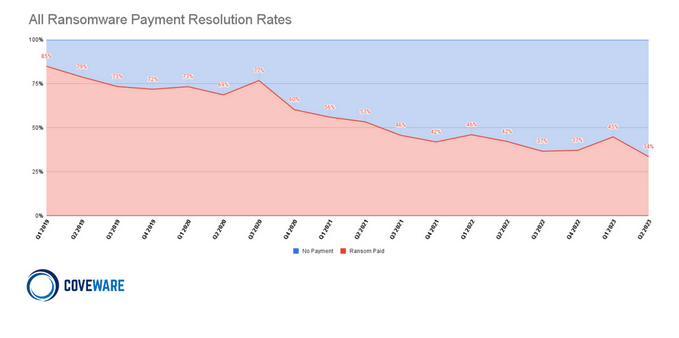
Figure 4 – Statistics of ransom payments in ransomware attacks. Source: Coveware.
Summary
The topic of ransomware is multifaceted, and providing a definitive answer on how companies should handle such incidents is challenging. Next week, we will discuss real examples of such attacks and examine how companies worldwide have dealt with such challenges. Until then!
Sources:

Helm for the Second Time – Versioning and Rollbacks for Your Application
We describe how to perform an update and rollback in Helm, how to flexibly overwrite values, and discover what templates are and how they work.
AdministrationInnovation

Helm – How to Simplify Kubernetes Management?
It's worth knowing! What is Helm, how to use it, and how does it make using a Kubernetes cluster easier?
AdministrationInnovation

INNOKREA at Greentech Festival 2025® – how we won the green heart of Berlin
What does the future hold for green technologies, and how does our platform fit into the concept of recommerce? We report on our participation in the Greentech Festival in Berlin – see what we brought back from this inspiring event!
EventsGreen IT